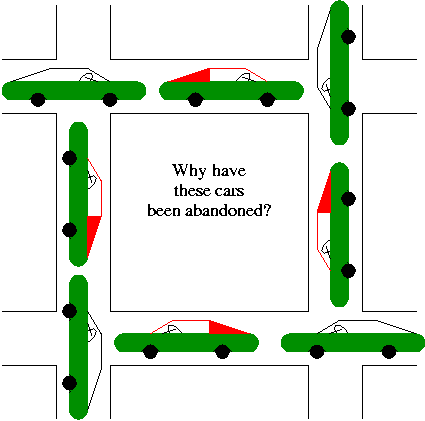
Deadlock in real situations
|
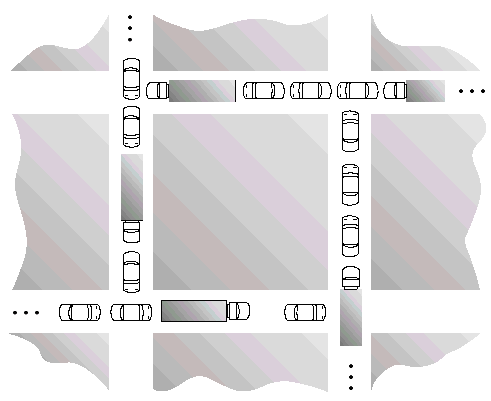
|

|
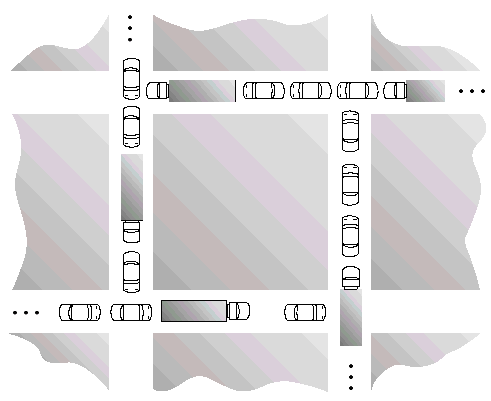
|
|
|
|
|
|
| Resource-Allocation Graph | Wait-For Graph |
|
|
|
|
|
| Non deadlock | Deadlock |
|
|
|
| Non deadlock | Deadlock |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| There is no process which its Request[i] ≤ work |
|
|
|
for i in range(0, n):
if Allocation[i] <> 0: Finish[i] = false.
else: Finish[i] = true.
/* ********************* 1 ************************** */
bool finish[N]; int work[M]; int i,j; bool flag=true;
work = Available
for(i=0; i<N; i++)
if(Allocation[i]!=0) finish[i]=false;
else finish[i]=true;
/* ********************* 2 ************************** */
flag=true;
while(flag==true){
flag=false;
for(i=0;i<N;i++)
if( (finish[i] == false) && (Request[i] <= work){
finish[i]=true;
work += Allocation[i];
flag=true;
}
}
}/* ********************* 3 ************************** */
flag = false;
for(i=0;i<N; i++)
if(finish[i] == false){ flag=true; cout<<"process "<<i<<" is deadlocked."<<endl; }
if(flag==true) cout<<"The system is deadlocked"<<endl;
else cout<<"The system is not deadlocked"<<endl;
N = 100 # number of Processes
M = 200 # number of Resources
Available = [0] * M # array(M)
Allocation = [[0] * M] * N # array(N,M)
Request = [[0] * M] * N # array(N,M)
################################################
finish = [False] * N #array(N)
work = Available.copy()
flag = True
for i in range(0, N):
if all(k == 0 for k in Allocation[i]):
finish[i] = True
################################################
while flag == True:
flag = False
for i in range(0, N):
if finish[i] == False and all(k<=m for k, m in zip(Request[i], work)):
finish[i] = True
work = [x+y for x, y in zip(work, Allocation[i])]
flag = True
################################################
deadlocked = [i for i in range(0, N) if finish[i] == False]
if len(deadlocked) !=0:
print("The system is deadlocked")
else:
print("The system is not deadlocked")
|
|
|
|
||||||||||||||||
MAX =
|
|
|
MAX =
|
|
|
||||||||||||||||||||||||||||||||
| Need = MAX - Allocation | Need =
|
Need =
Safe Sequence P1 , P0 , P2 |